Welcome to the resource topic for 2022/376
Title:
Universally Composable End-to-End Secure Messaging
Authors: Ran Canetti, Palak Jain, Marika Swanberg, Mayank Varia
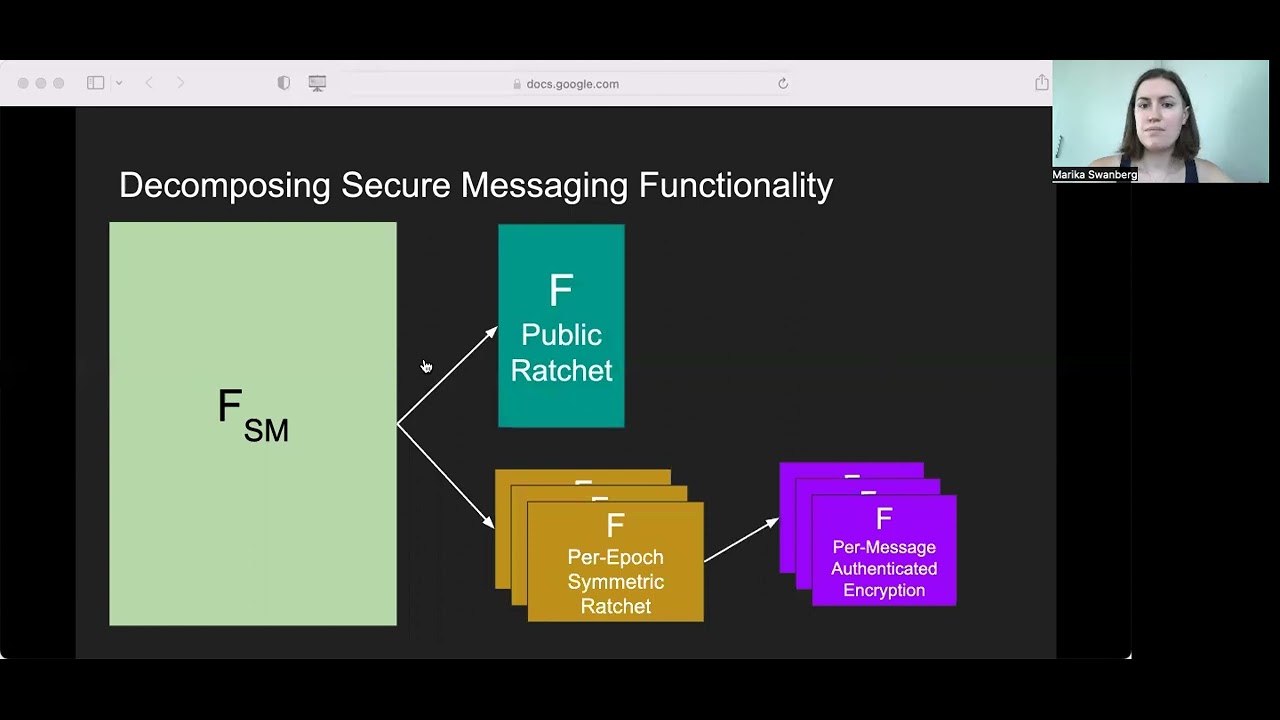
Abstract:We provide a full-fledged security analysis of the Signal end-to-end messaging protocol within the UC framework. In particular: (1) We formulate an ideal functionality that captures end-to-end secure messaging, in a setting with PKI and an untrusted server, against an adversary that has full control over the network and can adaptively and momentarily compromise parties at any time and obtain their entire internal states. In particular our analysis captures the forward and backwards secrecy properties of Signal and the conditions under which they break. (2) We model the various components of Signal (PKI and long-term keys, backbone “asymmetric ratchet”, epoch-level symmetric ratchets, authenticated encryption) as individual ideal functionalities that are analysed separately and then composed using the UC and Global-State UC theorems. (3) We use the Random Oracle Model to model non-committing encryption for arbitrary-length messages, but the rest of the analysis is in the plain model based on standard primitives. In particular, we show how to realize Signal’s key derivation functions in the standard model, from generic components, and under minimalistic cryptographic assumptions. Our analysis improves on previous ones in the guarantees it provides, in its relaxed security assumptions, and in its modularity. We also uncover some weaknesses of Signal that were not previously discussed. Our modeling differs from previous UC models of secure communication in that the protocol is modeled as a set of local algorithms, keeping the communication network completely out of scope. We also make extensive, layered use of global-state composition within the plain UC framework. These innovations may be of separate interest.
ePrint: https://eprint.iacr.org/2022/376
Talk: https://www.youtube.com/watch?v=FeTWJsbSeuU
See all topics related to this paper.
Feel free to post resources that are related to this paper below.
Example resources include: implementations, explanation materials, talks, slides, links to previous discussions on other websites.
For more information, see the rules for Resource Topics .