Welcome to the resource topic for 2020/1082
Title:
Beyond Birthday Bound Secure Fresh Rekeying: Application to Authenticated Encryption
Authors: Bart Mennink
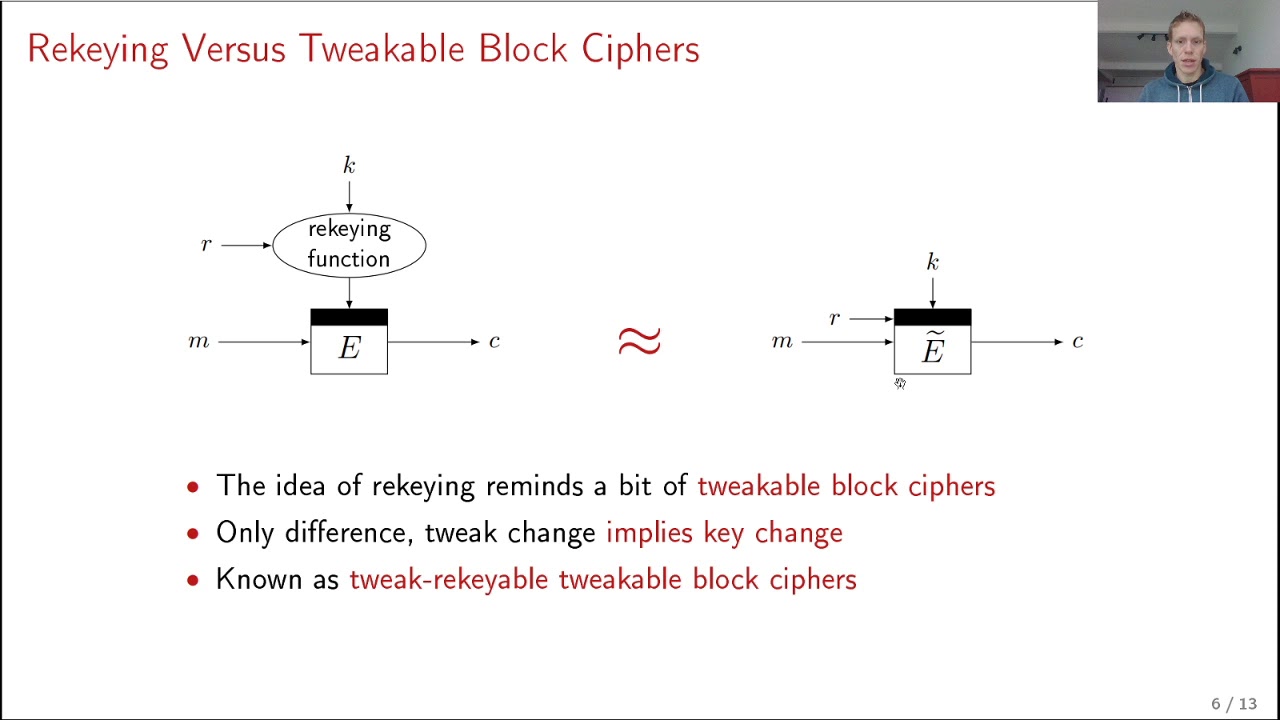
Abstract:Fresh rekeying is a well-established method to protect a primitive or mode against side-channel attacks: an easy to protect but cryptographically not so involved function generates a subkey from the master key, and this subkey is then used for the block encryption of a single or a few messages. It is an efficient way to achieve side-channel protection, but current solutions only achieve birthday bound security in the block size of the cipher and thus halve its security (except if more involved primitives are employed). We present generalized solutions to parallel block cipher rekeying that, for the first time, achieve security beyond the birthday bound in the block size n. The first solution involves, next to the subkey generation, one multiplication and the core block cipher call and achieves 2^{2n/3} security. The second solution makes two block cipher calls, and achieves optimal 2^n security. Our third solution uses a slightly larger subkey generation function but requires no adaptations to the core encryption and also achieves optimal security. The construction seamlessly generalizes to permutation based fresh rekeying. Central to our schemes is the observation that fresh rekeying and generic tweakable block cipher design are two very related topics, and we can take lessons from the advanced results in the latter to improve our understanding and development of the former. We subsequently use these rekeying schemes in a constructive manner to deliver three authenticated encryption modes that achieve beyond birthday bound security and are easy to protect against side-channel attacks.
ePrint: https://eprint.iacr.org/2020/1082
Talk: https://www.youtube.com/watch?v=va2o0g0ap1Y
Slides: https://iacr.org/submit/files/slides/2020/asiacrypt/ac2020/140/slides.pdf
See all topics related to this paper.
Feel free to post resources that are related to this paper below.
Example resources include: implementations, explanation materials, talks, slides, links to previous discussions on other websites.
For more information, see the rules for Resource Topics .