Welcome to the resource topic for 2013/723
Title:
Amplifying Privacy in Privacy Amplification
Authors: Divesh Aggarwal, Yevgeniy Dodis, Zahra Jafargholi, Eric Miles, Leonid Reyzin
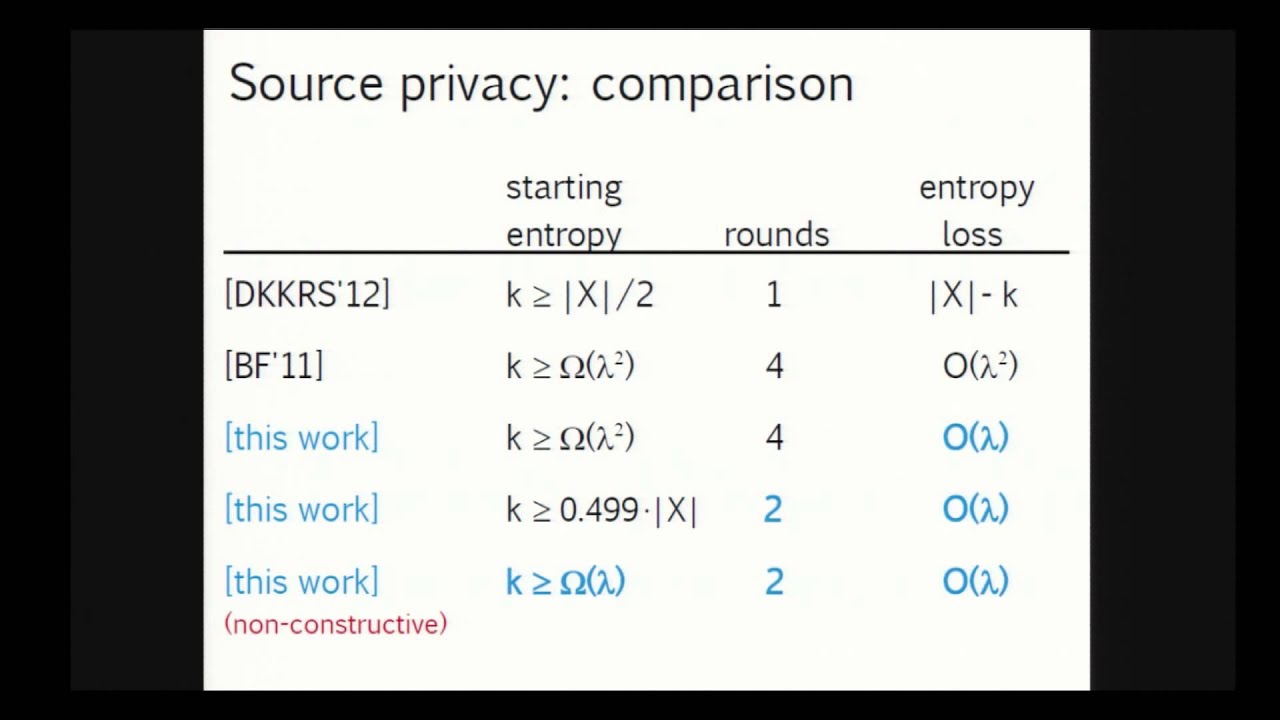
Abstract:We study the classical problem of privacy amplification, where two parties Alice and Bob share a weak secret X of min-entropy k, and wish to agree on secret key R of length m over a public communication channel completely controlled by a computationally unbounded attacker Eve. Despite being extensively studied in the literature, the problem of designing optimal'' efficient privacy amplification protocols is still open, because there are several optimization goals. The first of them is (1) minimizing the {\em entropy loss} $L=k-m$ (it is known that the optimal value for $L=O(\lambda)$, where $\eps=2^{-\lambda}$ is the desired security of the protocol). Other important considerations include (2) minimizing the number of communication rounds, (3) maintaining security even after the secret key is used (this is called {\em post-application robustness}), and (4) ensuring that the protocol $P$ does not leak some useful information’’ about the source X (this is called {\em source privacy}). Additionally, when dealing with a very long source X, as happens in the so-called Bounded Retrieval Model (BRM), extracting as long a key as possible is no longer the goal. Instead, the goals are (5) to touch as little of X as possible (for efficiency), and (6) to be able to run the protocol many times on the same X, extracting multiple secure keys. Achieving goals (1)-(4) (or (2)-(6) in BRM) simultaneously has remained open, and, indeed, all known protocols fail to achieve at least two of them. In this work we improve upon the current state-of-the-art, by designing a variety of new privacy amplification protocols, in several cases achieving {\em optimal parameters for the first time}. Moreover, in most cases we do it by giving relatively {\em general transformations} which convert a given protocol P into a ``better’’ protocol P'. In particular, as special cases of these transformations (applied to best known prior protocols), we achieve the following privacy amplification protocols for the first time: \begin{itemize} \item 4-round (resp. 2-round) {\em source-private} protocol with {\em optimal entropy loss} L=O(\lambda), whenever k = \Omega(\lambda^2) (resp. k > \frac{n}{2}(1-\alpha) for some universal constant \alpha>0). Best previous constant round source-private protocols achieved L=\Omega(\lambda^2). \item 3-round {\em post-application-robust} protocols with {\em optimal entropy loss} L=O(\lambda), whenever k = \Omega(\lambda^2) or k > \frac{n}{2}(1-\alpha) (the latter is also {\em source-private}). Best previous post-application robust protocols achieved L=\Omega(\lambda^2). \item The first BRM protocol capable of extracting the optimal number \Theta(k/\lambda) of session keys, improving upon the previously best bound \Theta(k/\lambda^2). (Additionally, our BRM protocol is post-application-robust, takes 2 rounds, and can be made source-private by increasing the number of rounds to 4.) \end{itemize}
ePrint: https://eprint.iacr.org/2013/723
Talk: https://www.youtube.com/watch?v=KBKvcvlQ_F8
See all topics related to this paper.
Feel free to post resources that are related to this paper below.
Example resources include: implementations, explanation materials, talks, slides, links to previous discussions on other websites.
For more information, see the rules for Resource Topics .