Welcome to the resource topic for 2012/366
Title:
Securing Circuits Against Constant-Rate Tampering
Authors: Dana Dachman-Soled, Yael Tauman Kalai
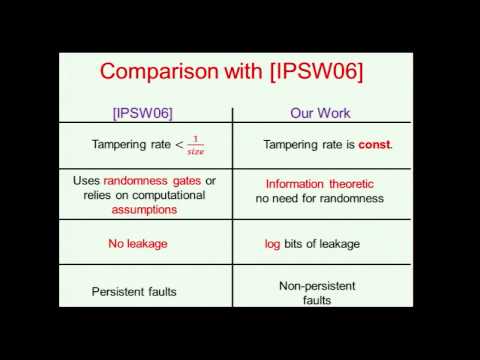
Abstract:We present a compiler that converts any circuit into one that remains secure even if a constant fraction of its wires are tampered with. Following the seminal work of Ishai et al. (Eurocrypt 2006), we consider adversaries who may choose an arbitrary set of wires to corrupt, and may set each such wire to 0 or to 1, or may toggle with the wire. We prove that such adversaries, who continuously tamper with the circuit, can learn at most logarithmically many bits of secret information (in addition to black-box access to the circuit). Our results are information theoretic.
ePrint: https://eprint.iacr.org/2012/366
Talk: https://www.youtube.com/watch?v=28Y2ehkok98
Slides: https://iacr.org/cryptodb/archive/2012/CRYPTO/presentation/9-2-Kalai.pdf
See all topics related to this paper.
Feel free to post resources that are related to this paper below.
Example resources include: implementations, explanation materials, talks, slides, links to previous discussions on other websites.
For more information, see the rules for Resource Topics .