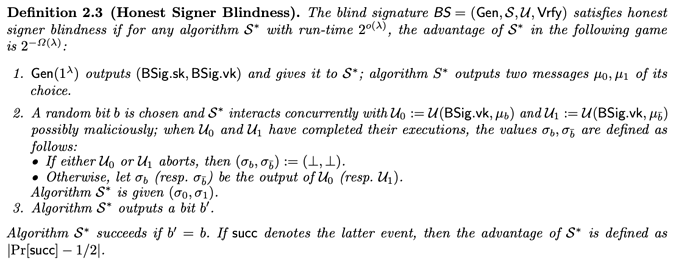
The recent 2023-077 paper proposes a lattice-based blind signature. In Sec. 2, they propose the following definition of anonymity for blind signatures:
The paper they refer, 2021-1565, also proposes a lattice-based blind signature, but it relies on a different definition of anonymity for blind signatures:
Another lattice-based blind signature protocol, 2022-834, uses a similar definition with attacker-controlled messages.
Crucially, the two definitions differ in the source of the messages to be signed: in 2021-1565, the messages are chosen by the attacker, while in 2023-077 the definition holds “for every two messages”, which suggest that the attacker does not know the messages.
The two definition seem to be quite different, as it is easy to imagine a protocol that is apparently secure wrt one definition but not the other. Indeed, with the 2023-077 definition, it’s sufficient for the signer not to extract the original messages, while with the 2021-1565 definition, the signer should not be able to link the final signature to any protocol execution.
So, have I misunderstood something and the two definitions are actually equivalent? Or if not, are there consequences in terms of blind signature applications, and is one definition more commonly used?